The rise in cyber-attacks and increasingly stringent compliance regulations shows that mobile and web apps must take data security more seriously. Data encryption is a fundamental aspect of strong mobile app and web app security. Read on to learn how you can safeguard your mobile apps using encryption.
Over 54% of web traffic now comes from mobile, seeing significant growth and shifts in mobile use patterns as a result of the global pandemic and ongoing digital transformation in businesses. Consumers today demand an increasingly personalized digital experience, fueling the growth of mobile and web apps. However, such personalization requires access to personal data – and in the rush to approaching web and mobile app development faster, security may be overlooked.
Mobile and web app data security is the process of safeguarding end-user data from attack, breach, malware, or other manipulation or loss. One of the most fundamental aspects of mobile and web app security is data encryption.
This guide will answer the question “what is data encryption?” as well as more specifically “what are some best practices to protect the data in your mobile apps?” The guide will detail the three states of data, how web app security differs from mobile app security, specifics of implementing data encryption, as well as the latest cryptography techniques and multi-factor authentication.
What is Data Encryption?
Data encryption is the process of transforming digital information from plain text into an incomprehensible format known as ciphertext. This process of encoding (transforming) data uses what is known as a “key” – a piece of information, usually numbers and/or letters, generated by a cryptographic algorithm (a set of rules).
Encrypted information can only be read (decrypted back into readable format) by someone with a decryption key.
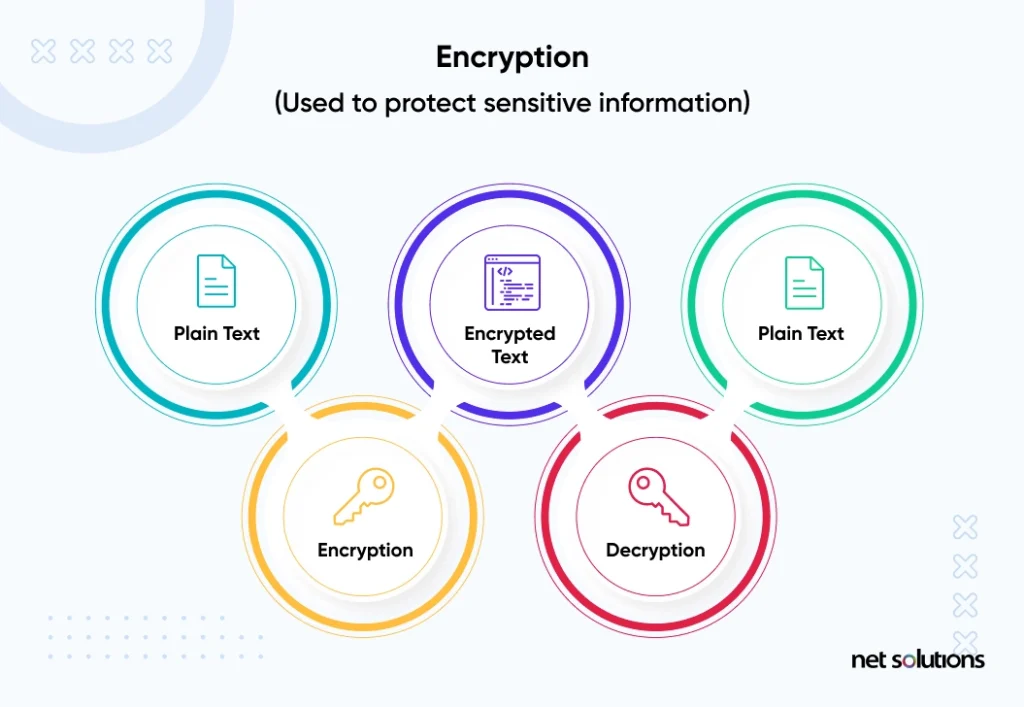
Although encryption does not by itself prevent cyber attacks from accessing a system, it makes the data held in the system or the data being transmitted safe to anyone who may access or intercept it.
“Network and data security are essential in today’s environment of increasingly open and interconnected systems, networks, and mobile devices. Critical security services include confidentiality, identity authentication, data integrity authentication, source authentication, and the support of non-repudiation. Cryptographic techniques can offer such protection for data that is sensitive, has a high value, or is vulnerable to unauthorized disclosure or undetected modification during transmission or while in storage.”
Methods of Encryption
In general, there are two methods of encryption:
- Symmetric encryption uses a single key to encrypt and decrypt data
- Asymmetric or public key encryption uses a separate key for encrypting and decrypting data. The encryption key is known as a public key; the decryption key is known as a private key.
Common Encryption Standards
The strength of the encryption depends on the algorithm being used, the size of the key, the generation of the key, and the key exchange process. Common encryption standards include:
1. Data Encryption Standard (DES) – Now deprecated
A symmetric-key algorithm of 56 bits in length. Developed in the early 1970s, this is considered a weak standard because of its short key size.
2. Triple DES – Now deprecated
Also known as TDES, 3DES, or Triple DEA, this is a symmetric-key block cipher that applies the DES cipher algorithm three times to each data block, but still with a 56-bit key length. The National Institute of Standards and Technology (NIST) has deprecated DES and 3DES for new applications and requires a phase-out of all applications by 2023.
3. RSA
A public-key encryption system named for its founders, with the public key based on two (secret) large prime numbers along with an auxiliary value, with the secret primes required for decryption. Used commonly for apps that require digital signatures.
4. Advanced Encryption Standards (AES)
Also known as Rijndael, a symmetric-key algorithm and variant of the block cipher by the same name, AES is the standard adopted by the US Government / NIST. AES leverages a family of ciphers with different key and block sizes. Most encryption tools rely on AES encryption.
5. Blowfish & Twofish
Although it is only 64-bit block size, Blowfish is popular in software development, specifically for databases and file encryption. Twofish is a symmetric cipher algorithm that was created to replace Blowfish, using 128-bit block size and supporting larger keys that are more resistant to brute force attacks.
Knowing which type of encryption to use is about choosing a secure option – and that will change over time as algorithms evolve to the emerging risk landscape – but also the right option for the application. For example, the larger the key, the more secure it is – but also the greater chance that performance can be impacted.
The Three States of Mobile & Web App Data
When it comes to mobile data security and data encryption, it is important to identify where and when encryption should be applied. There are three main data states where data encryption should be applied, in addition to strong multi-factor authentication, identity management, and access controls.
The three states of data should be considered for all types of sensitive or privileged data, including employee data, consumer data, financial or health data, and intellectual property.
1. Data At Rest
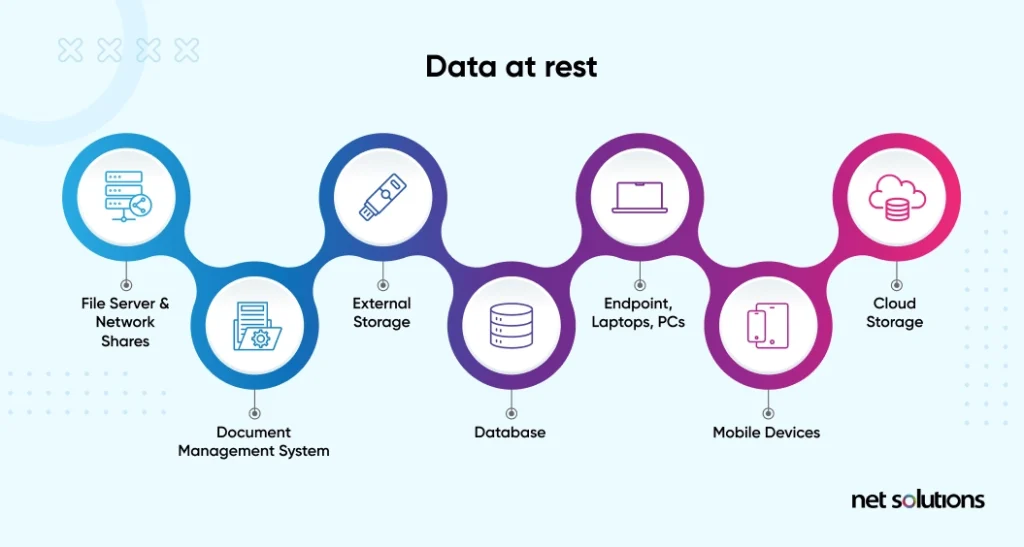
Data at rest is data that is inactive – it is not being moved between devices or networks. Data at rest is held in storage on file servers, in databases and document management systems, on endpoints, or in cloud storage. Data at rest includes all physical storage devices, including backups.
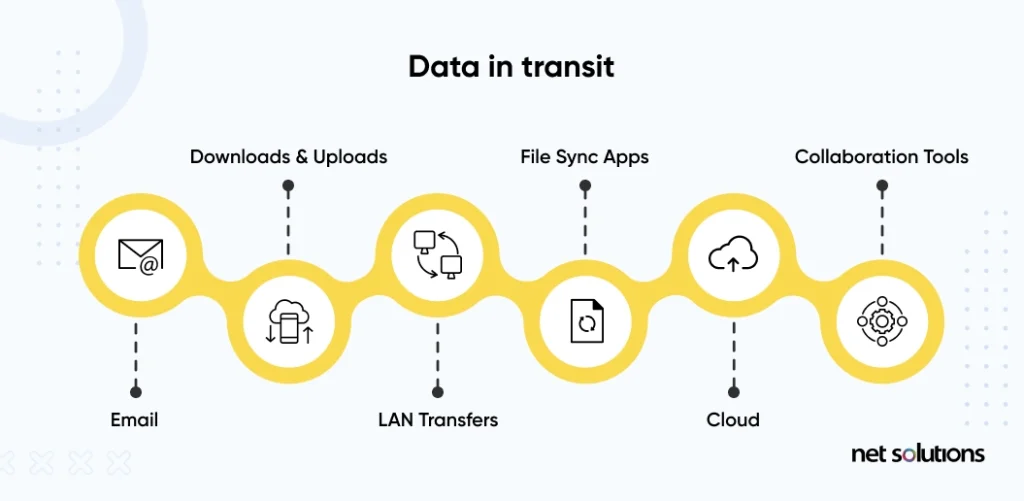
2. Data In Transit
Data in transit is data that is moving from one place to another, also referred to as data in motion. Data in transit may move over a public connection (over the Internet), through a private network, or between networks or devices. This is considered the most at-risk data state for accidental or malicious data loss.
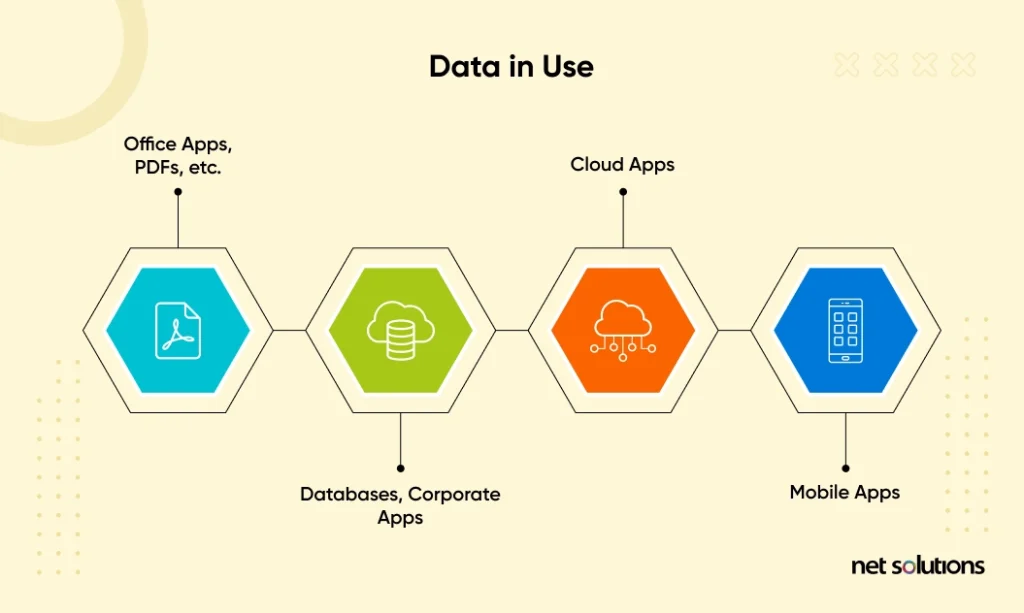
3. Data In Use
Data in use refers to any data that is active – data that is in computer memory or is being actively accessed, updated, processed, or deleted by a system.
Why Protect Mobile And Web App Data
Web and mobile app development companies must prioritize data privacy and compliance in accordance with several strict regulations – or face not only an erosion of trust with their users and potentially irreversible brand damage but also significant fines. Further, in the case of mobile app security, the fact that the code runs from the operating system of the endpoint (mobile device) introduces risks to intellectual property (IP).
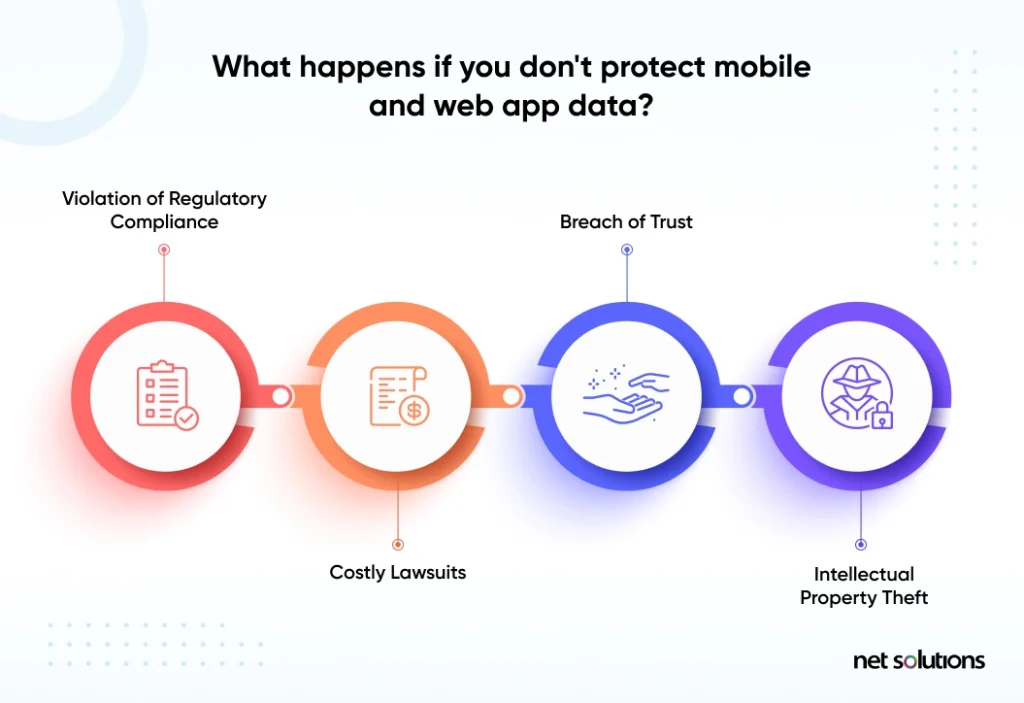
What is Mobile & Web App Compliance?
Compliance is the practice of following the regulations set forth by governments or industry organizations. Data compliance, often impacts the collection, use, storage, and integrity of data about the end-user, with specific requirements depending on the sensitivity of that data (e.g. personally identifiable information, financial data, protected health information) as well as rules over data sharing, end-user access to that data, and the right to be forgotten.
Regardless of where the app is created or used, there are several regulatory requirements that should be consulted with regard to end-user privacy and security, including the GDPR, CCPA, CPRA, PIPEDA and the specific guidelines and requirements from app stores (Google, Apple). The advice of online articles, including this one, does not replace the guidance of a lawyer.
Why Is Web App Security Different From Mobile App Security?
Although both a web app and a mobile app are accessed from a mobile device or smartphone, the architecture of each app is significantly different – impacting the approach to data encryption and the other available tools and practices to improve mobile app security.
A web app is a dynamic website, changing the display based on inputs or actions of the end-user, but the application runs on a server with only a small part of the application accessible to the end-user (the front-end). Due to this, traditional security tools such as firewalls can add layers of protection to the data in a web app.
Web apps leverage secure socket layers (SSL) and transport layer security (TLS) to establish encrypted links between networked computers. The SSL certificate (TLS certificate) is a digital certificate (a public key certificate) that authenticates a website’s identity and establishes that encryption connection between a web server and a browser.
A mobile app, in contrast, is downloaded and installed onto a mobile device – a process that increases the attack surface from one instance (the server) to many endpoints (each mobile device) – endpoints over which the developer has no security control. This increased attack surface is combined with the greater amount of data being collected and stored by the mobile device (vs the browser). A mobile app is more vulnerable to having vulnerabilities discovered and compromises introduced or infiltrating communication between the app and the back end systems to gain access to a wider pool of sensitive data.
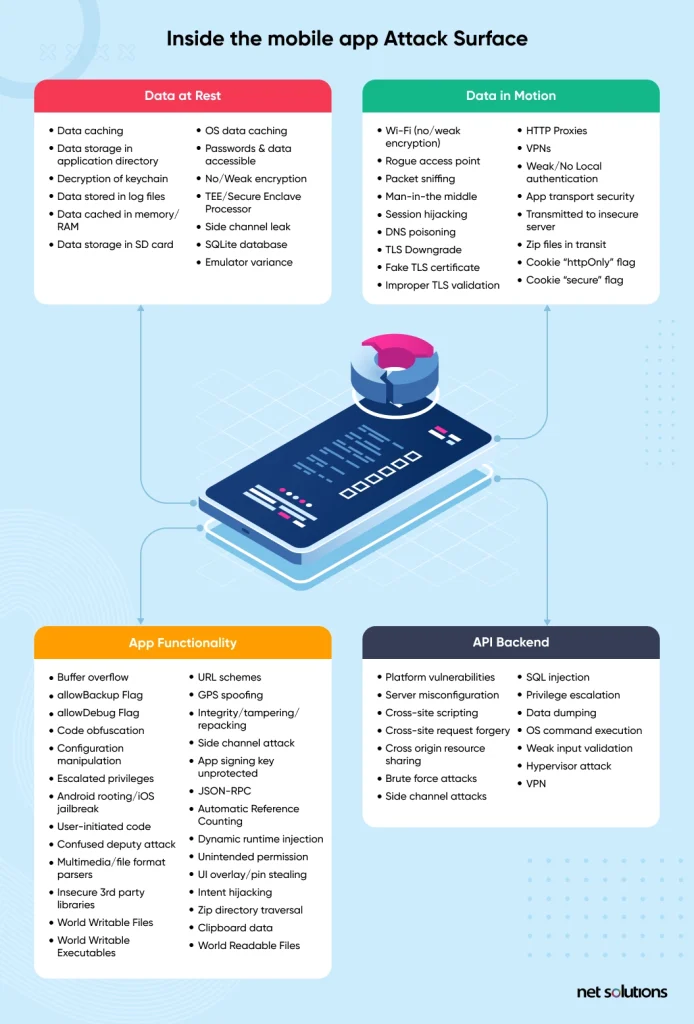
Although there is much more to consider for mobile app security, the vast majority of risk points can be protected by encrypting sensitive data in all its stages: at rest, in transit, and in use.
How To Protect Data In Mobile & Web Apps Using Encryption
In balancing the needs of the organization to create a secure app that meets compliance requirements and consumer privacy concerns, mobile app developers have turned to encryption to protect against threats.
The following lays out best practices for using encryption and other mobile app security tips:
1. Source Code Encryption
There are two common attacks against source code: one, attackers from injecting malware into vulnerabilities or bugs in the source code, or two, attackers exfiltrate the code to repackage the app (with malware) to new unsuspecting users. Source code encryption is the act of protecting the intellectual property (source code) of the web or mobile app against exfiltration (theft), manipulation, or compromise by the attack by making the code or files/strings in the code unreadable – and thus unusable by cyber attackers.
2. Manage Keys Securely
Key management best practices involve many steps to protect the entire lifecycle of the cryptographic keys (generation, exchange, storage, use, destruction, and replacement) – after all, what is the point of locking your doors (encryption) if you are not going to keep your keys secure.
Best practices for encryption key management include adopting the following tips, or leveraging a key management system (KMS) to automate several of these tasks:
- Develop policies and systems for key management
- Choose the correct algorithm and key size for each encryption use case
- Define a crypto period, a fixed time span during which a key is authorized for use
- Secure physical access to the key servers
- Use a dedicated external key management system such as an HSM or other hardware key management device or software / virtual appliances that do the same, to ensure the keys are separate from the data
- Ensure a random number generator meets the highest standards (refer to NIST) for key generation
- Update or rotate encryption keys regularly (depending on use)
- Retire unused keys to reduce any undue risk
- Restrict access to keys to only those who need it, with proper user authentication, or require a minimum number of people to approve certain operations
- Leverage KMIP (key management interoperability protocol) for secure key distribution with encrypted key transport on a TLS channel or offline in a split component distribution
- Bind permissions to each key to ensure they have limited uses (e.g. only signing, encryption, decryption, etc)
- Always keep audit logs of key creation, use, and deletion
For more guidance on key management, refer to NIST SP 800-57.
3. File-Level & Database Encryption
Research has demonstrated that up to 76% of mobile applications have insecure data storage that puts sensitive end-user information (passwords, personal data, financial information) at risk, and potentially in violation of compliance regulations. Therefore It is important to ensure that unstructured data stored in the local file systems and/or databases on the mobile device are encrypted against vulnerabilities.
The goal of file-level and database encryption is to both protect the data and to make the database-less attractive since the data would become meaningless to cybercriminals.
4. Use The Latest Cryptography Techniques
The risk landscape is constantly evolving as technology changes and cybercriminals keep trying to “crack” existing security protections. In order to build an adequate level of security, developers must stay on top of trends in cryptography and perform regular penetration testing and threat modeling to ensure encryption (and other protections) is working.
Although AES is the current trusted standard, one leveraged by the US government, there are still researchers working on new and emerging standards such as ECC (elliptic curve cryptography), which is already seeing acceptance by the NSA for key exchange and digital signatures.
5. Multi-Factor Authentication
Hand-in-hand with encryption is the need for strong multi-factor authentication for both end-users as well as internal users, particularly those with privileged levels of access. Following the zero trust model, “never trust, always verify,” choose at least two factors of authentication for users. Ideally, your app can offer users more than one way to authenticate and authenticate with their most preferred strong option such as a hardware token.
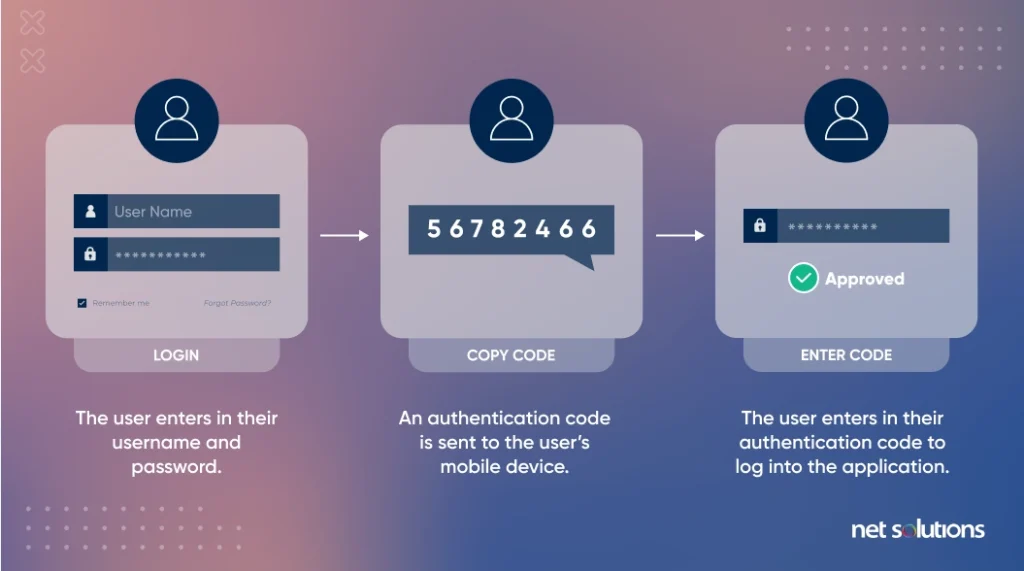
For the most privileged users such as those with admin rights to alter code or access customer data, consider stronger forms of authentication that do not rely on legacy authentication (passwords) or mobile devices, but instead leverage a hardware token that is phishing-resistant.
6. Use FIPS 140-2 Encryption for Government Apps
FIPs 140-2 refers to the Federal Information Processing Standard Publication, a security standard used to approve cryptographic modules that include both hardware and software components. FIPS 140-2 defines four levels of security for applications that could be used by government agencies to protect sensitive but unclassified data. App developers can seek to become “FIPS 140-2” validated for use by government agencies.

FIPS 140-2 has since been superseded by FIPS 140-3, but as yet no application has been validated against this new standard. Testing against the new standard began in 2021.
Frequently Asked Questions
1. What Is The Difference Between A Web App And Mobile App?
Before further detailing encryption for mobile and web apps, let’s first step back and define what we mean by a web app and a mobile app:
- Unlike the static content of a website, which is the same for all users, a web app is dynamic, changing the display based on user inputs or actions such as placing an order, logging in, downloading a document, making a payment, or filtering search results.
- A mobile app is downloaded and installed onto a mobile device, designed either for a specific platform (Android, iOS), known as a “native app,” or cross-platform (works on multiple platforms). When a user downloads the app, it gains access to system resources and data on that device, making security an even higher concern.
2. Are Mobile Apps More Secure Than Web Apps?
As stated above and throughout this guide, mobile app security is very different from web app security. Mobile apps must protect more kinds of information about the user and guard against a much larger attack surface. Although web app security is much more straightforward, the actual security of the web app depends on how well security is applied in each instance.
3. Do Apps Encrypt Data?
It is recommended that mobile and web apps encrypt data at rest, in transit, and in use. Users can also take additional measures to protect their app by setting a password or PIN for it.
4. What are the best practices to Secure Your Customers’ Data using Web & Mobile App Encryption?
- Understand data technologies and databases, and leverage them into your website/mobile app.
- Identify and classify sensitive data so that you can take the best measures to protect it.
- Your website/app must have a strong data usage policy in place.
- Use the principle of least privilege to restrict unauthorized access.
- Leverage data encryption no one can easily decode data even if they get their hands on it.
- Allow data backup to ensure customers can retrieve data just in case any breach happens.
SHARE THIS POST
Table of Contents
Related Resources
- What is App Store Optimization (ASO)? The in-depth guide for 2024
- The Mobile App Architecture Guide for 2024
- 7-Step Mobile App Development Checklist (Free Download)
- How Much Does it Cost to Build an App [A Complete Breakdown]
- eCommerce Mobile App Development: A Step-by-Step Guide
- 7-Step Mobile App Development Checklist (Free Download)
- How Firebase is Emerging as an Innovation in App Development
- A Complete Guide to Implementing In-App Purchases
- Low-Cost Mobile App Development: A Comprehensive Guide
- How to Make an App in 2024: 5 Stages of Mobile App Development
- What is Mobile-first Design (+9 Best Practices)
- The Ultimate Guide for New App Ideas
- Offshore Mobile App Development: An In-Depth Guide
- Most Popular Programming Languages for Mobile App Development
- The 7 Best Programming Languages to Write & Develop Native Android Apps
- 7 Mobile App Development Tips for Acquisition & Retention
- Top 15 Mobile App Development Trends to Watch for in 2024
- The Fundamentals of Android App Development: Basic Tutorial

