Summary: Just because software is feature-rich doesn’t mean it is also safe from security threats. That’s why you must pay close attention to software security testing. Read on to learn what software security testing is, why it is essential, and what approaches and tools you can use to perform it efficiently.
“The number of serious vulnerabilities in open-source software and third-party libraries continues to increase at a rate that makes remediation nearly impossible for teams that don’t adopt measures for tracking third-party component use.” – WhiteHat Security.
In current times when incidents of security breaches are on the rise, building security into your software is essential. It is possible only if businesses work towards a powerful software security testing approach for their apps and any other digital product that can receive critical data from customers, clients, and partners.
Here’s everything you need to know about software security testing and how you can make the most out of it:
What is Software Security Testing?
“Testing is an infinite process of comparing the invisible to the ambiguous in order to avoid the unthinkable happening to the anonymous.”— James Bach.
Software security testing is a type of software testing approach that ensures the software is free of any potential vulnerabilities or weaknesses, risks, or threats so that the software might not harm the user system and data.
Performing software security tests, often multiple times is a prerequisite for publishing software today.
Why is Software Security Testing Required?
None of the users, business people, entrepreneurs, or organizations want to lose any information or data due to the security leaks of software. Just because a piece of software meets quality requirements related to functionality and performance does not necessarily mean that your web app software is secure. Software testing, in today’s scenario, is a must to identify and address application security vulnerabilities to maintain the following:
- Security of information, databases, data history, and servers
- Customers’ trust and integrity
- Protection of web applications from future attacks
Software Security Testing: The Approach
While preparing and planning for security tests, a developer can take the following approaches:
- Architecture Study & Analysis: The first step is understanding whether the software complies with the requirements.
- Classify Threats: List all potential threats and risk factors you must test.
- Test Planning: Run the tests based on the identified threats, vulnerabilities, and security risks.
- Testing Tool Identification: Software security testing tools for web applications; the developer needs to identify the relevant tools to test the software.
- Test Case Execution: After performing a security test, the developer should fix them manually or use any suitable open-source code.
- Reports: Prepare a detailed test report of the security tests you performed. It would contain a list of the vulnerabilities, threats, and issues resolved and the ones that are still pending.
Types of Software Security Testing
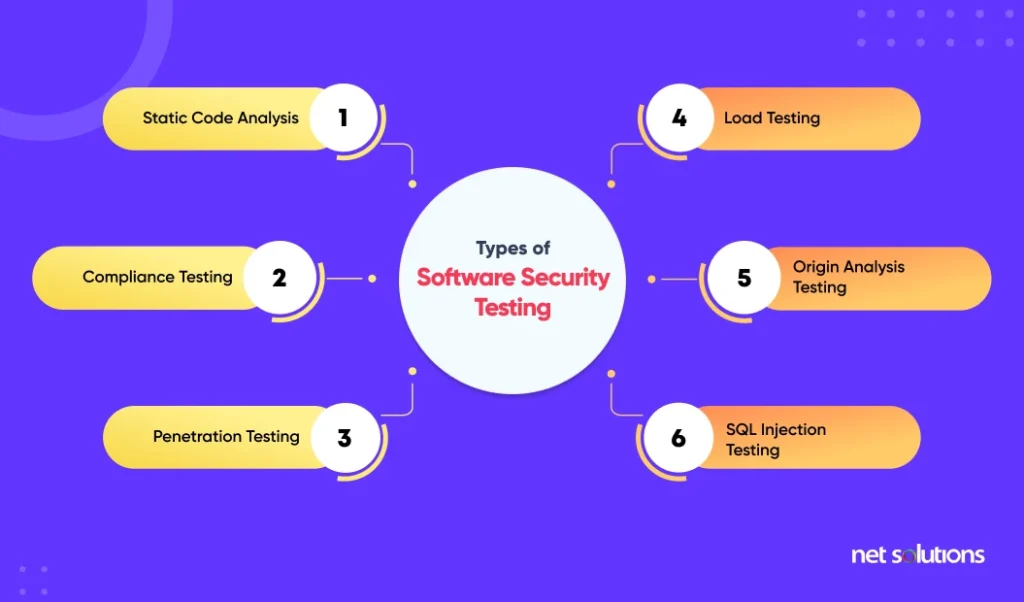
The most common web app software security tests from a few years ago might not be practical today. Let’s look at the different security tests that are relevant today. We follow several web application security testing types simultaneously.
1. Static Code Analysis
This is the oldest approach and the first type of security testing most developers perform. We can perform this test manually, and developers can read through the code to find potential security flaws.
2. Compliance Testing
It’s essential for software to meet a client’s predefined policies, and we ensure this by running compliance tests. In these tests, we analyze a piece of software by comparing it with the actual configurations.
3. Penetration Testing
This software testing involves simulation attacks against newly designed software to identify the weak points. Once detected, a developer fixes the bugs within the codes.
4. Load Testing
This test measures how a piece of software performs under a heavy load. The reason behind this test is Distributed-Denial-of-Service (DDoS), an attack that aims to disrupt application availability by application or its host infrastructure with traffic or other requests.
5. Origin Analysis Testing
The popularity of open-source software has grown in the past few years. This software security testing helps developers and security admins determine where a given piece of code originated. Such testing becomes relevant when some of your source code has come from a third-party project or repository.
6. SQL Injection Testing
SQL Injection test can be done for apostrophes, brackets, commas, or quotation marks. These simple errors lead to attacks by spammers. SQL injection attacks are critical because attackers can enter the server database and get vital information.
It is not a definitive list of security tests. Enterprises might perform other security tests like Risk Assessment, Posture Assessment, Security Auditing, and even Ethical Hacking.
Software Security Testing Responsibilities
A software security tester’s key responsibility is to protect the software data from unauthorized access and ensure if any breach happens, they can easily counter it.
Here are a few other responsibilities a software security tester has to do:
- Working with their clients from the beginning to understand their testing requirements, such as the types of devices the software will operate on.
- Planning and creating penetration methods, scripts, and tests.
- Conducting software remote and on-site testing to identify and fix security issues.
- Simulating security breaches to gauge whether your software can withstand them or not.
- Listing reports and recommendations to the management or the development team to fix them as soon as possible.
- Continuously renewing the company’s incident response and emergency recovery methods.
Tools for Security Testing
Software security tools for testing are widely available in the market today. These security test tools are software in themselves. Some of the tools are also open-source.
1. Zed Attack Proxy (ZAP)
It is a multi-platform, open-source security testing tool for web applications developed by the Open Web Application Security Project (OWASP).

Key features of ZAP
- Automatic scanning
- Easy to use
- Multi-platform
- Rest-based API
- Support for authentication
2. Wfuzz
This tool is developed using Python and has no GUI in its interface. One problem with this tool is that this is usable only via the command line.
Key features of Wfuzz
- Authentication support
- Cookies fuzzing
- Multi-threading
- Multiple injection points
- Support for proxy and SOCK
3. Wapiti
It is one of the easiest tools to operate for newcomers and perform testing services. Wapiti is one of the leading web application security testing tools, free of cost, and an open-source project in SourceForge.
Wapiti injects payloads to check whether the script is vulnerable or not. Users can find a whole lot of information and instructions in SourceForge.
Key features of Wapiti
- Supports both GET and POST-HTTP methods for attacks
- Can give colors in the terminal to highlight vulnerabilities
- Has different levels of verbosity
- Fast and easy way to activate/deactivate attack modules
- Adding a payload can be as easy as adding a line to a text file
4. W3af
It is another top-rated tool built with python. This tool is specifically perfect for web applications. W3af can detect over 200 types of security issues.

Besides, it can detect:
- Blind SQL injection
- Buffer overflow
- Cross-site scripting
- Insecure DAV configurations
5. SQLMap
It is an entirely free-to-use tool that automates the detection of a vulnerability in a website’s database. With the help of a very powerful testing engine, SQLMap can detect various security threads in a web app.
Key features of SQLMap:
- Automates the process of finding SQL injection vulnerabilities
- Can also be used for security testing on a website
- Robust detection engine
- Supports a range of databases, including MySQL, Oracle, and PostgreSQL
There are other tools too for the software security testing process which are not so efficient but can be used for cross-testing – Arachni, Grabber, Nogotofail, SonarQube, and IronWasp are worth mentioning.
How to Evaluate Software Security Testing?
To know whether your software security initiatives are successful or not, you must measure them against the following key metrics:
1. Vulnerabilities in Code Over Time
It refers to the security issues you’ve discovered in your code after applying techniques like penetration testing and various software security testing tools.
2. Vulnerability Density
Vulnerability density is the number of security issues in particular lines of code. This metric can compare risk on different systems, languages, or technology platforms.
3. Vulnerabilities with High Severity
With this software security testing metric, you can categorize vulnerabilities by their potential impact on data confidentiality, integrity, and system availability. As a result, you know which issues you should pick first.
4. Mean-time to Repair
The average time you take to fix the vulnerabilities is the mean time to repair. The longer time for resolving issues means you need to fasten your software security testing effort.
5. Percentage of Vulnerabilities Fixed
It refers to how many software security vulnerabilities you fixed. With this metric, you can measure the efficiency of your software security testing effort.
6. Flaw-creation Rate
The flaw creation rate refers to the rate at which flaws are created. We compare mainly to compare it to the mean time to repair. The idea is to ensure we’re fixing issues faster than the rate at which we’re finding them because otherwise, you’re in trouble.
How can Net Solutions Help You with Software Security Testing?
The prime objective of security testing is to forecast a system’s vulnerability and determine whether its data and resources are protected from potential intruders. With Security testing software services, you can identify the implementation errors that were not discovered during the code reviews.
Providing a thorough software security analysis makes it crucial to team up with organizations that can help build your organization’s reputation, customer confidence, and trust. If you’re looking for someone, we can help. We can also support you with exhaustive reports and dashboards, rendering remedial measures for your data security challenges. Talk to us to avail our software security services.
Frequently Asked Questions
Software vulnerabilities can happen due to two primary reasons:Flaws in the program design, such as a loophole in the logic function. Error in the program source code.
A security tester identifies potential threats to ensure they can be fixed on time and users’ precious information remains safe from malicious attacks.
Security audits, vulnerability assessments, and penetration tests are three types of security audit assessments. Also, while we use these terms interchangeably, they are different types of tests.
Programming is not a necessity in security testing. However, it is a valuable skill that can improve your worth as a software security tester and make you more efficient in your work.



